Understanding Cybersecurity Threat Actors

1. Introduction
As the digital landscape evolves, cyber threats have become a critical concern for governments, businesses, and individuals. Threat actors, entities responsible for malicious activities in cyberspace, vary significantly in their motivations, capabilities, and methods. This white paper examines three primary categories of threat actors: nation-state actors, state-sponsored actors, and non-state actors. Understanding these groups is crucial for developing effective cybersecurity strategies and defenses.
2. Nation-State Actors
Definition: Nation-state actors are directly employed or operated by a government to conduct cyber operations that align with national interests. These actors often belong to a nation's intelligence, military, or law enforcement agencies and have access to significant resources and expertise. They are often known for their advanced persistent threat (APT) activity.
Characteristics:
- Sophistication: Highly skilled with access to advanced tools, techniques, and infrastructure.
- Objectives: Engage in cyber espionage, intelligence gathering, sabotage, and disruption of critical infrastructure. They may also conduct operations to influence public opinion, steal intellectual property, or prepare for potential cyber warfare.
- Funding and Resources: Benefit from substantial government funding, allowing for sustained and sophisticated campaigns.
Examples:
- Russia's APT29 (Cozy Bear): Involved in espionage activities targeting governments, research institutions, and companies.
- China's APT41: Active since at least 2012, Known for its dual-purpose operations targeting intellectual property theft and espionage.
Typical Tactics: Nation-state actors employ advanced persistent threats (APTs), sophisticated phishing campaigns, zero-day vulnerabilities, and supply chain attacks.
3. State-Sponsored Actors
Definition: State-sponsored actors are cybercriminal groups or hackers that receive support, funding, training, or protection from a government. While they act in the interests of the sponsoring nation, they maintain a level of independence, providing the state with plausible deniability.
Characteristics:
- Semi-autonomous: Operate with guidance or directives from a government but are not formal employees.
- Objectives: Often overlap with nation-state actors but may also pursue financial gain, political disruption, or other goals aligned with state interests.
- Flexibility: These actors can adapt to changing missions, allowing them to target a wide range of industries, including financial, energy, technology, and healthcare.
Examples:
- North Korea's Lazarus Group: Engaged in cyber operations for financial gain and espionage, often targeting cryptocurrency exchanges and financial institutions.
- Iranian hacker groups: Conduct operations to disrupt regional adversaries and steal sensitive information. Example: CyberAv3ngers
Typical Tactics: State-sponsored actors may employ ransomware, spear-phishing, distributed denial-of-service (DDoS) attacks, and malware deployment.
4. Non-State Actors
Definition: Non-state actors are independent individuals, groups, or organizations that conduct cyber activities without any formal government affiliation. Their motivations can range from financial gain to ideological beliefs, hacktivism, or personal challenge.
Characteristics:
- Varied skill levels: Capabilities can range from amateur hackers to highly organized cybercriminal groups.
- Diverse motivations: Financial gain, ideological causes, hacktivism, or even thrill-seeking.
- Flexible targets: Willing to attack any target that aligns with their objectives or offers lucrative opportunities.
Examples:
- Anonymous: A hacktivist group known for targeting organizations and governments to promote social and political causes.
- REvil: A ransomware gang that has targeted companies worldwide to extort large sums of money.
Typical Tactics: Non-state actors frequently use ransomware, phishing, malware distribution, DDoS attacks, and data breaches.
5. Comparative Analysis
Figure 1: Comparison Table of Threat Actors
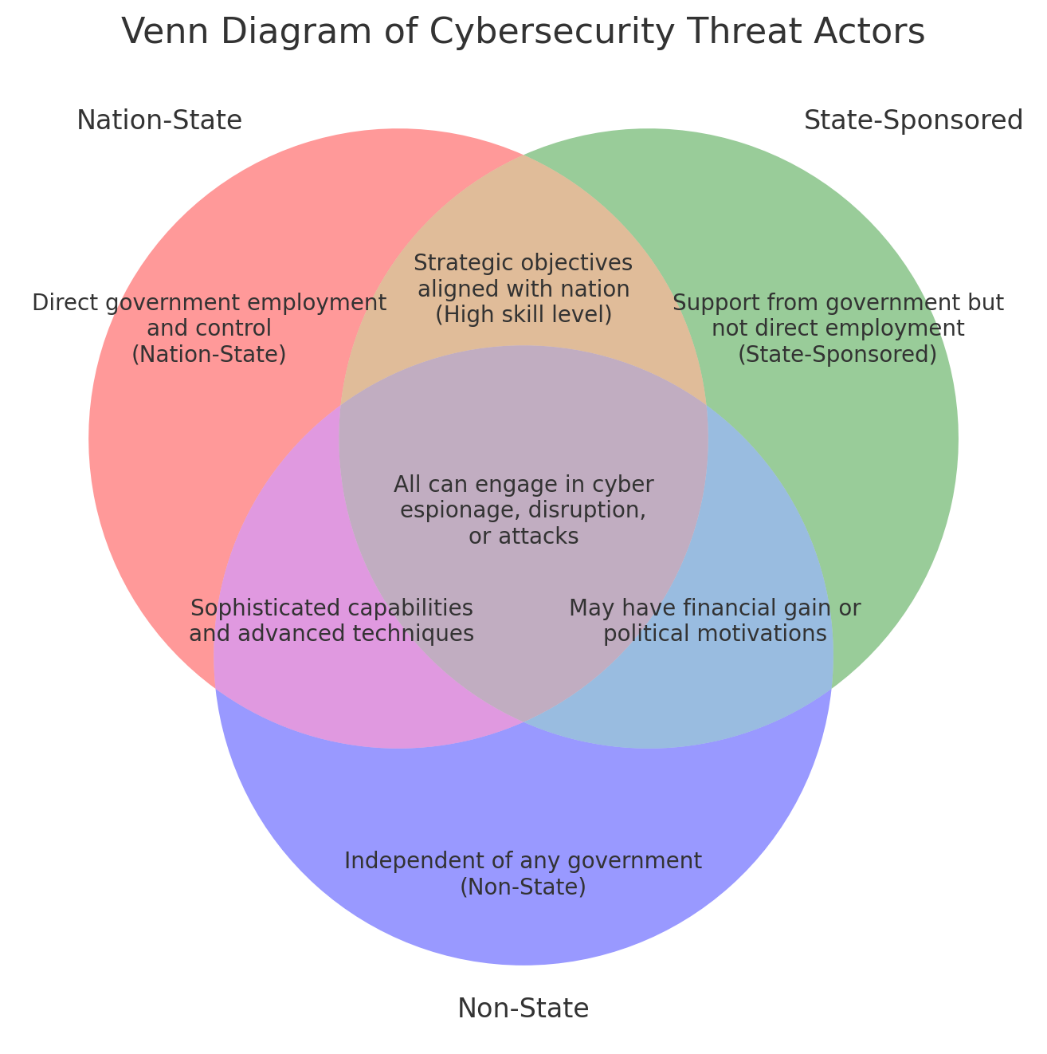
Nation-State:
- Direct government employment and control (Nation-State)
State-Sponsored:
- Support from government but not direct employment (State-Sponsored)
Non-State:
- Independent of any government (Non-State)
Overlapping areas:
- Strategic objectives aligned with nation (High skill level) - between Nation-State and State-Sponsored
- All can engage in cyber espionage, disruption, or attacks - center of all three
- Sophisticated capabilities and advanced techniques - between Nation-State and Non-State
- May have financial gain or political motivations - between State-Sponsored and Non-State
6. Conclusion
Nation-state, state-sponsored, and non-state actors represent distinct yet overlapping categories of cyber threat actors. Understanding their characteristics, motivations, and tactics is essential for developing a robust cybersecurity strategy. While nation-state and state-sponsored actors present more sophisticated and targeted threats, non-state actors can be just as dangerous due to their unpredictable behavior and potential for financial and reputational damage.
As cyber threats continue to evolve, organizations and governments must remain vigilant, adapt to emerging risks, and employ a layered defense strategy to protect against these diverse and dynamic adversaries.
7. Recommendations
Threat Intelligence: Stay informed about the latest tactics, techniques, and procedures (TTPs) used by different threat actors to adapt defenses accordingly.
Incident Response Plans: Develop and regularly update incident response plans to address the unique challenges posed by each type of threat actor.
Collaboration: Foster collaboration between government agencies, private sector entities, and international partners to enhance threat detection and response capabilities.


